**KeyMux**
Features
==============================================================
Easily and securely integrate secure key enclaves (hardware security
modules, smart cards, security tokens, secure elements, and
cryptoprocessors; local and network-attached) into your workflow. KeyMux
seamlessly connects where your keys are securely held with the tools you
wish could easily use them.
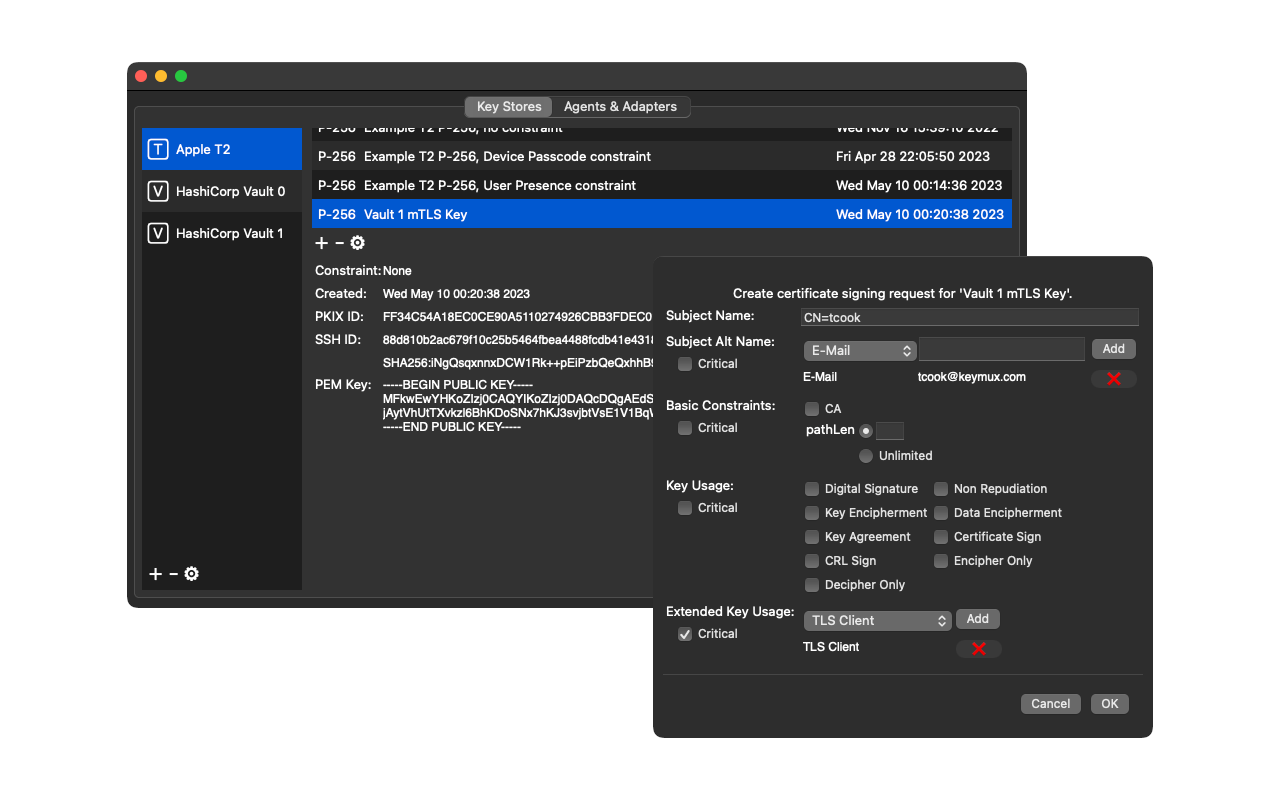
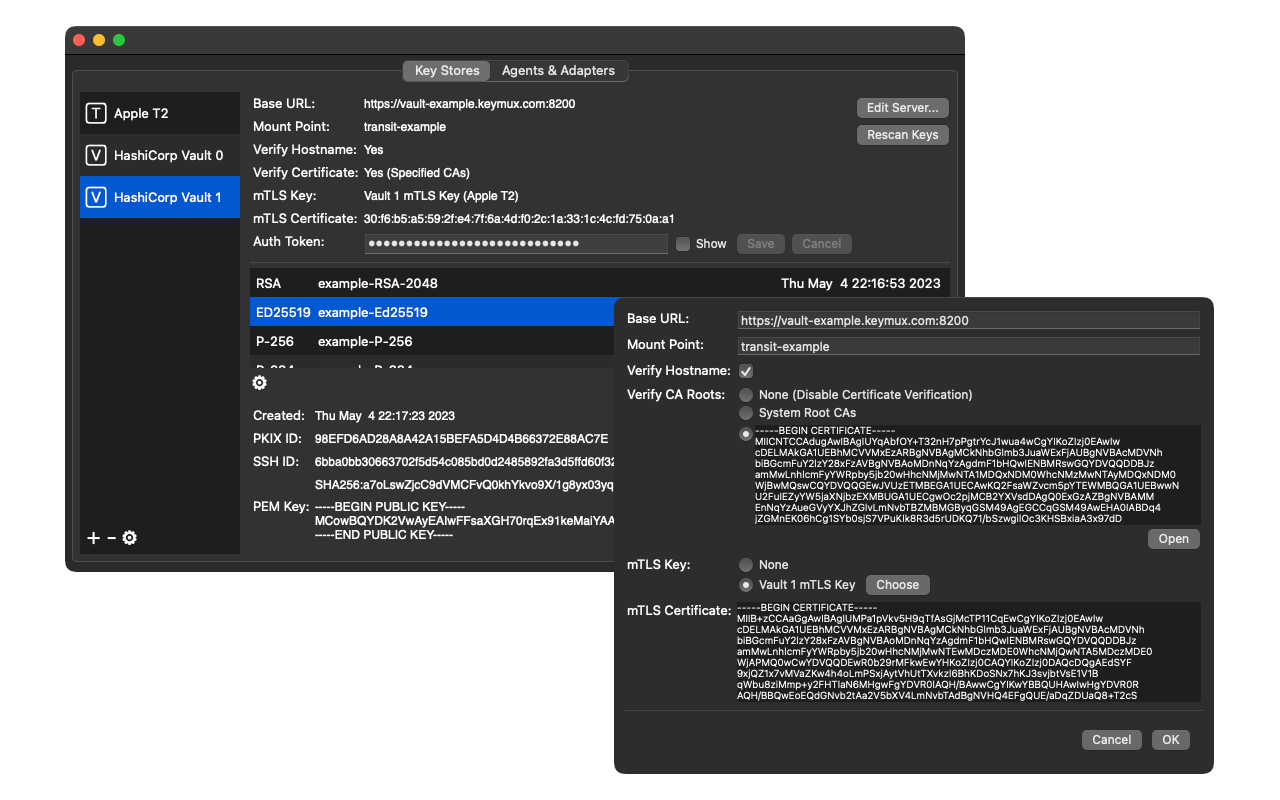
* Key Stores
- Apple T2 Security Chip
- Hashicorp Vault - with mTLS authentication using other enclaved keys
- PIV Smartcards (coming soon)
- KMIP Servers (coming soon)
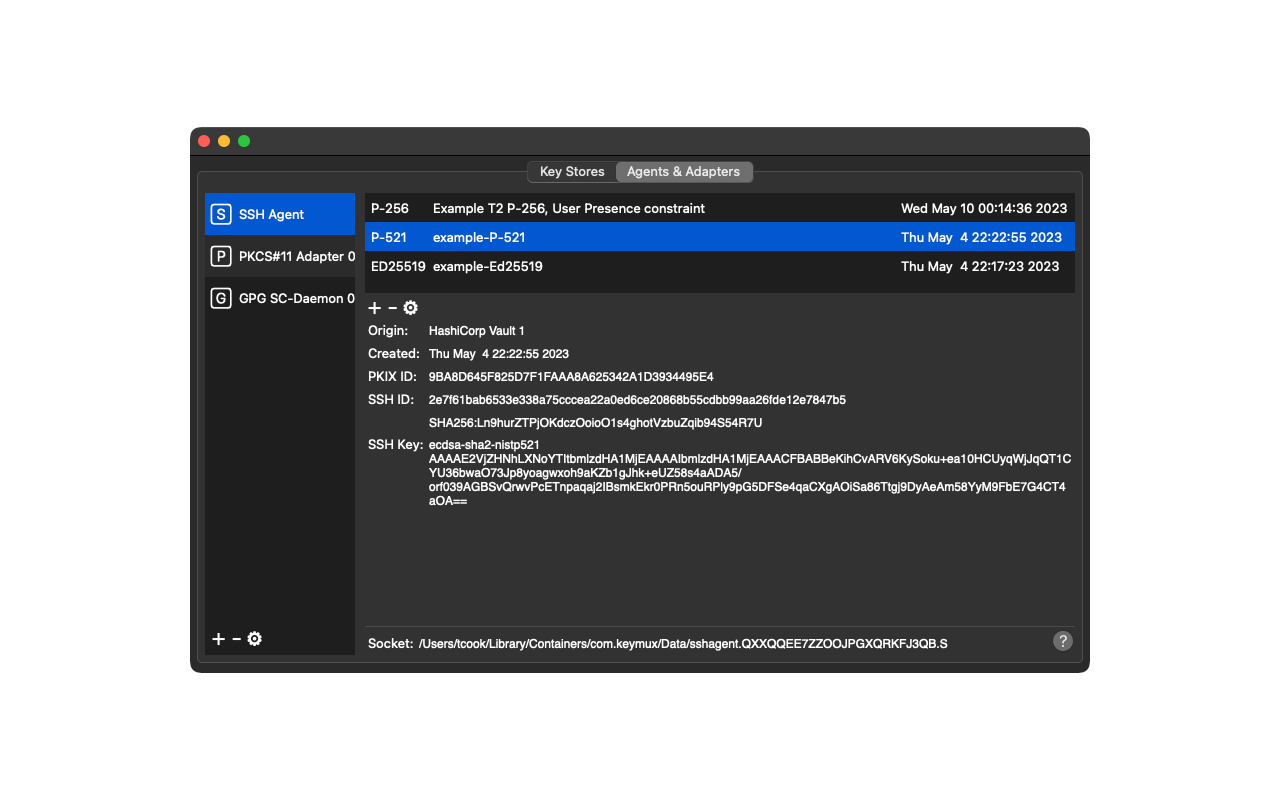
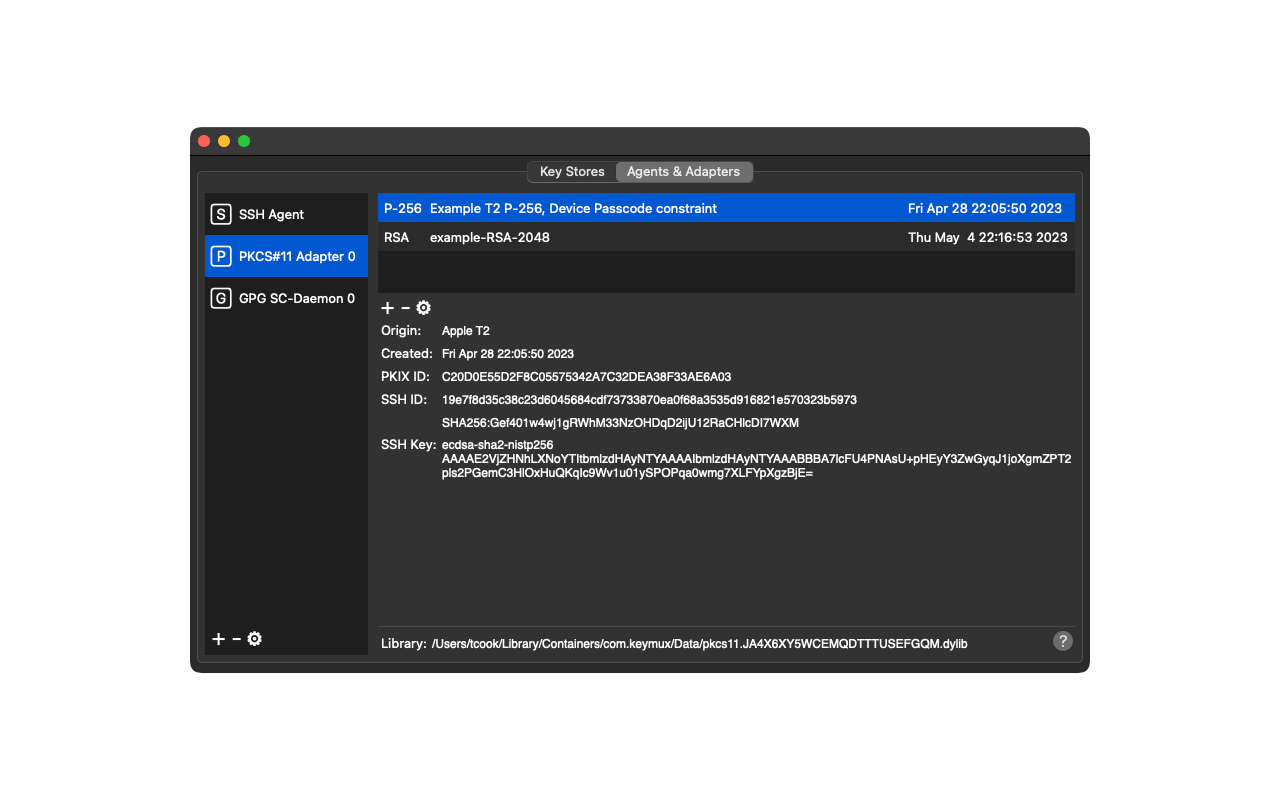
* Application Agents & Adapters
- OpenSSH Agent
- PKCS #11 Module
- GnuPG SC-Daemon
When private keys are exposed even momentarily to infrastructure software,
best practice is frequent key rotation. But this is costly, complex, a
common source of automated infrastructure issues, and an ideal target for
achieving persistence. Ultimately, key rotation doesn't address the root of
the problem--any private key visible outside a secure key enclave should be
presumed compromised from the very first moment; even asymmetric (RSA, ECC)
keys effectively become as vulnerable as software-embedded plaintext
passwords. Like FIDO for website authentication, KeyMux can help you deploy
an end-to-end hardware-secured key management and key usage solution for
your network and cloud infrastructure, without the confusion, complexity,
and unsafe compromises which have plagued enterprise key management for
decades. While newer secure enclave solutions such as laptop-integrated
secure elements, Hashicorp Vault, Yubikeys, and AWS KMS provide welcome
improvements in enclave usability, they only solve part of the problem, and
even exacerbate complexity with their disparate interfaces.
Example use cases:
* Now your team can use network-attached shared enclaved keys for AWS SSH
logins or PGP signing of software packages.
* Use enclaved keys from OpenSSL, Curl, and other commonly used software
supporting PKCS #11.
Screenshots
==============================================================
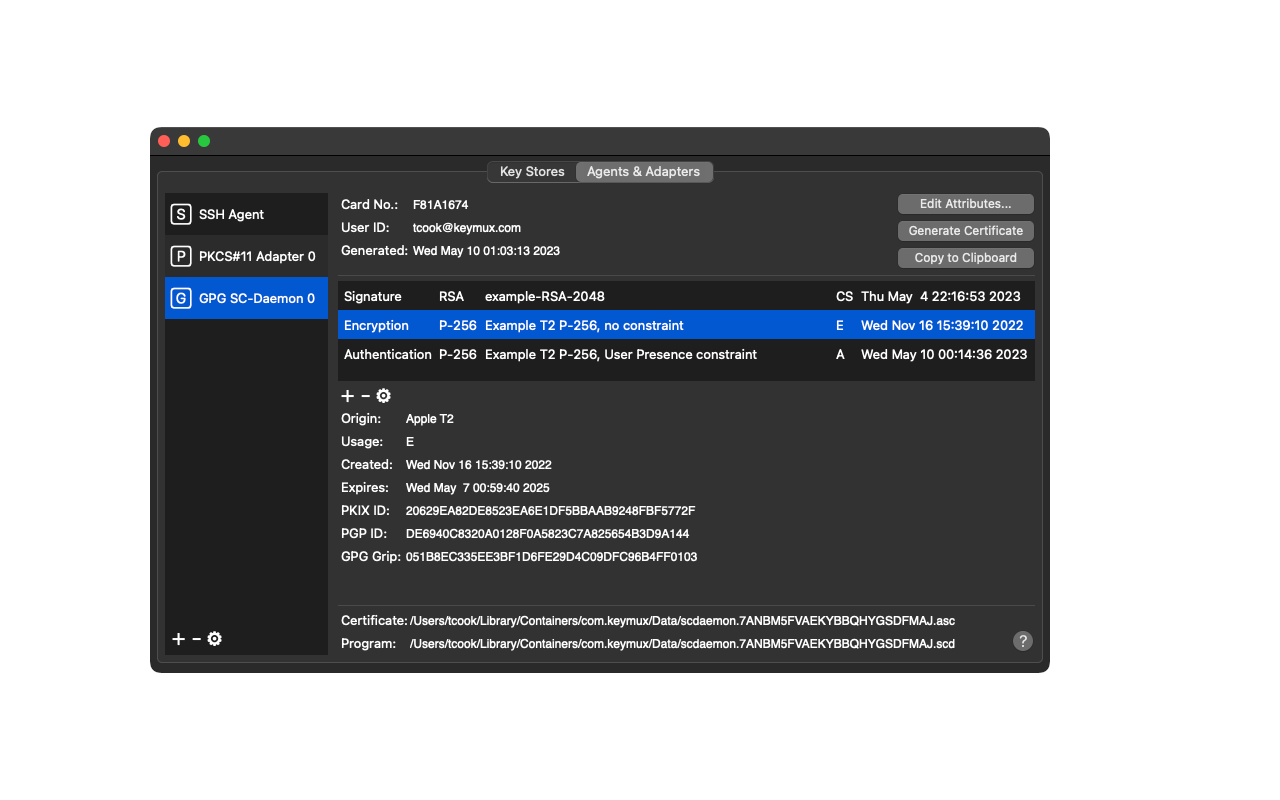
Matrix
==============================================================
| Apple T2 | Hashicorp Vault | PIV Cards | AWS KMS | KMIP
--------------|-------------|-------------------|-------------|---------|------
**OpenSSH** | ECDSA | ECDSA, RSA, EdDSA | Coming Soon | "" | ""
**PKCS #11** | ECDSA | ECDSA, RSA | Coming Soon | "" | ""
**GnuPG** | ECDSA, ECDH | ECDSA, RSA | Coming Soon | "" | ""
Notes:
* Apple T2 only supports NIST P-256 ECC keys.
* Hashicorp Vault Transit engine does not support ECC key exchange (ECDH, X25519), nor the RSA decryption mode required by PGP.
* OpenSSH supported through both an SSH Agent service or PKCS #11 module.
* PKCS #11 support for ECDH and RSA decryption/encryption is forthcoming.
* GnuPG supported through an SC-Daemon replacement adapter.
Platforms
==============================================================
KeyMux currently supports macOS. Support for Windows is planned for the near
future. Custom solutions for Linux user and server environments are
available. Please contact info@keymux.com for more details.
Download
==============================================================
KeyMux is [available on the Mac App Store](https://apps.apple.com/us/app/keymux/id6448807557).
Support
==============================================================
See our our support page [here](support.html).
About
==============================================================
Hitzke Labs, LLC
220 Montgomery St, STE 1087
San Francisco, CA 94104
info@hitzkelabs.com
Privacy Policy
==============================================================
See our our privacy policy [here](privacy.html).